CVE-2019-17004—Semi Universal XSS affecting Firefox for iOS
This bug allowed an attacker to potentially execute malicious JavaScript on arbitrary origins.
There is a kind of security flaw in Web browsers and extensions that can enable an attacker to bypass the same-origin policy[1] checks and take over your online activity by simply having you visit a web page; allowing accessing your bank account, learning about your search queries on Google, your emails, your messages on Facebook, etc. It can even enable the attacker to impersonate you and perform actions on your behalf. These flaws are called: Universal Cross-Site Scripting[2].
In October 2019, we discovered such a security flaw in Firefox for iOS, which allowed malicious actors to execute JavaScript on arbitrary origins.
Cliqz browsers are based on Firefox, and from time to time we conduct security and privacy audits of upstream projects, other browsers and our own products across platforms. These audits allowed us to discover some critical issues in the past[3].
In November last year, the Cliqz browser for iOS was undergoing a complete overhaul. While auditing the app for security issues during its development phase, we discovered a Universal Cross-Site Scripting (UXSS) vulnerability.
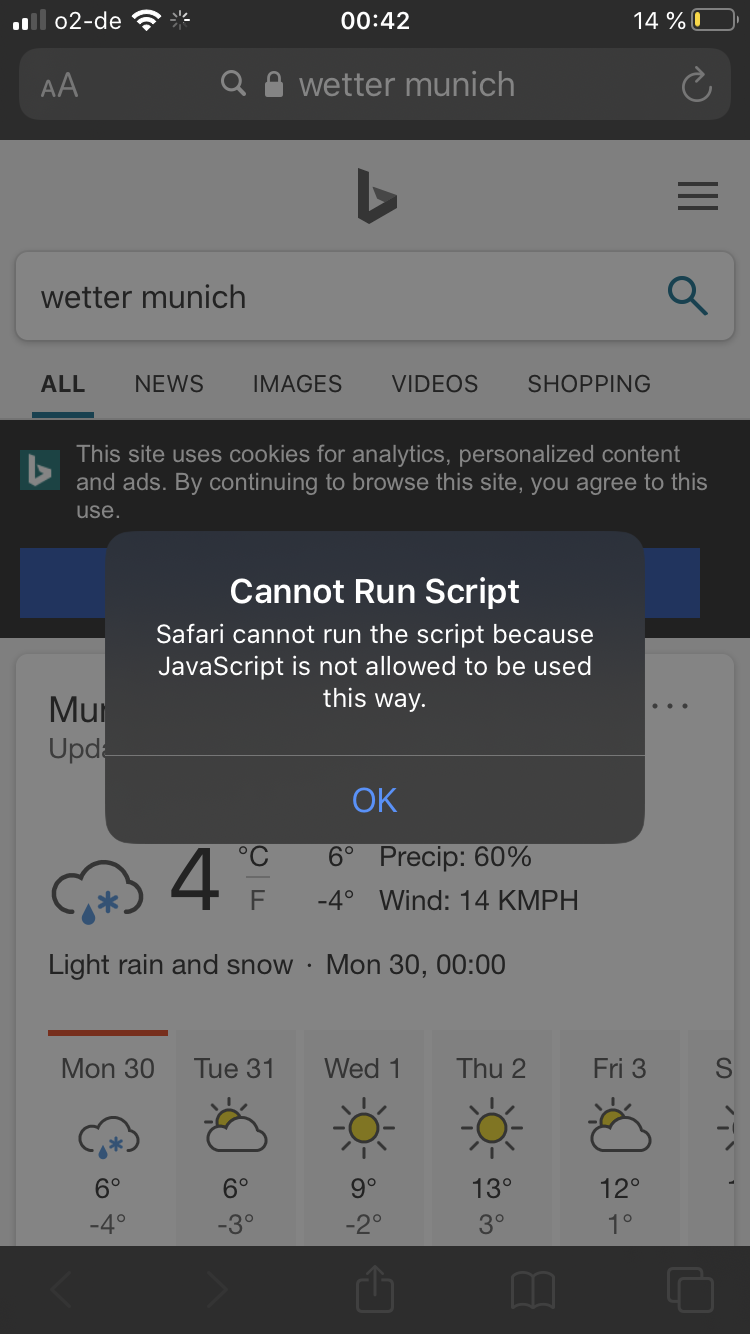
We tested the production version of Firefox (Version 19.1 - 16203) and realized that it had the same vulnerability, therefore we reported the issue via the Client Security Bug Bounty Program to Mozilla. At that time we tested a few other popular browsers on iOS and none of them had this issue. Some of them, like Safari, were even explicit in their error reporting :)
However, in January this year, when we were about to publish our findings, we did our due diligence and performed a sanity check on popular iOS browsers again. We found that this time Brave for iOS suffered from the same security issue. After reporting the issue to Brave, they promptly fixed it, but we wanted to wait for a few more months before publishing the details about this security issue to give users time to update to the latest version.
The Attack
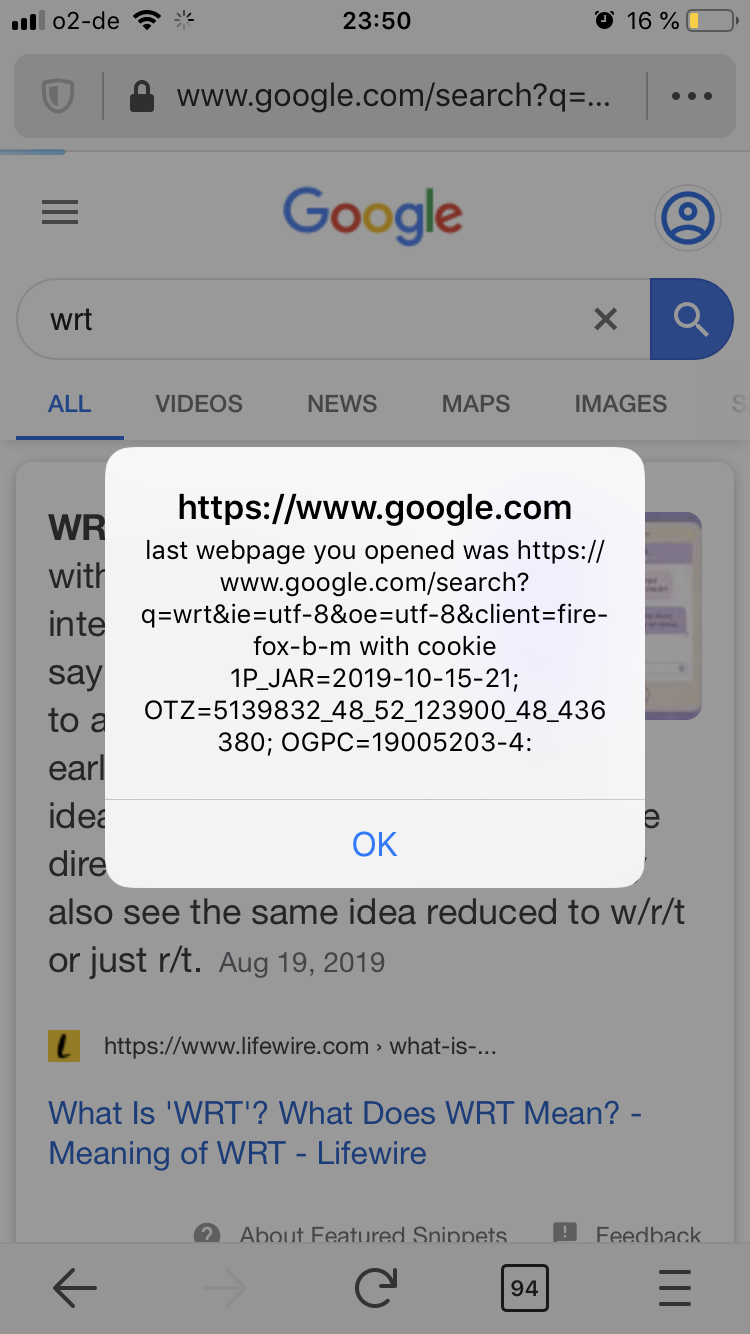
- Let’s imagine the user (victim) opens Firefox for iOS, and does a query on default search engine (In this example: https://www.google.com/).
- The user then visits an attacker-controlled website in the same tab—by either pasting a link, selecting a link from the webpage or any other means.
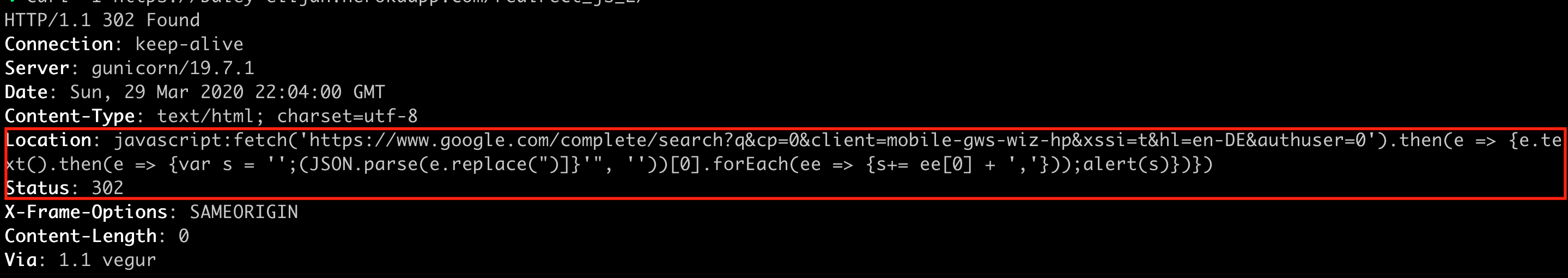
- This website returns the following malicious response
Locationheader:
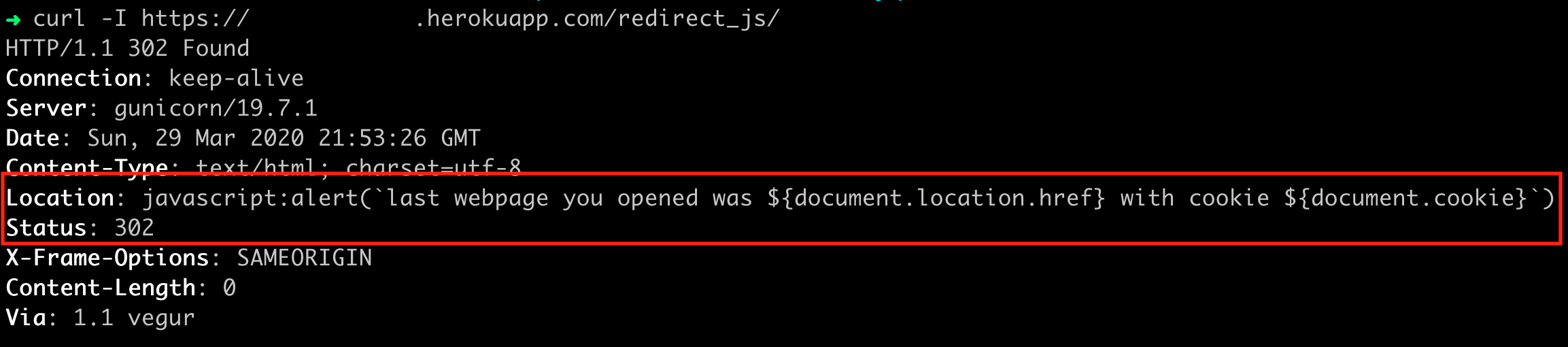
- Because of a bug in the browser, an attacker is able to execute JavaScript in the context of the previously visited website (i.e.
google.comin this case) by returning a redirect tojavascript: doEvil,
Being able to execute JavaScript on a different origin, opens a wide range of attacks. For example, not only can the attacker read sensitive data like cookies or the URL from webpages. They can also return JavaScript which performs API requests to retrieve information such as the last 10 queries that the user has submitted on google.com.
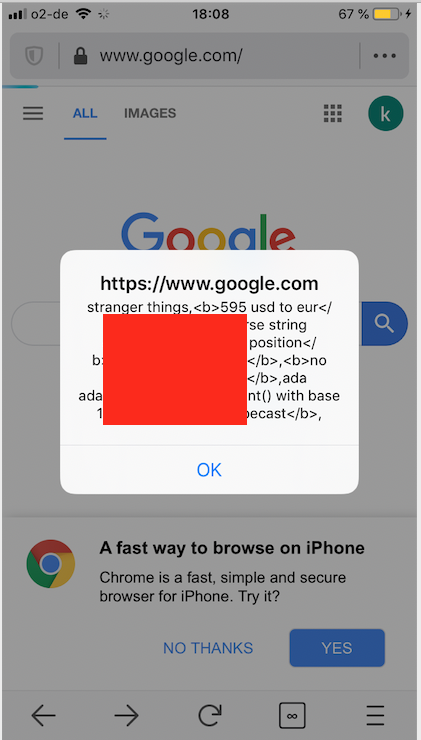
It is important to note that this issue only classifies as semi-UXSS because attackers cannot steal data from any website of their choice, but are limited to the last visited domain. For example, in the above case, if the attacker returns a JavaScript code in location header, that tries to steal data or execute actions on https://meine.deutsche-bank.de/trxm/db/, the attack will only work as long as the last website visited in that tab was https://meine.deutsche-bank.de/.
However, even given the above limitations the attacker can curate special links and lure the users into opening these malicious links by sharing them on social media, chat platforms, etc. If the user clicks on such links on these websites, the attacker can now try and exfiltrate sensitive user data from the website where the link was clicked from.
Given the impact of the vulnerability, the fact that it was present in production versions and was easily exploitable, Mozilla classified this bug as sec-critical[4].
Cause
The issue here was that Firefox for iOS had insufficient checks to block JavaScript from being executed when returned via Location response header. This bug originated from the bookmarklets functionality[5] added in Firefox for iOS. In order to fix this security issue, Firefox decided to remove this functionality altogether from the browser.
Timeline
UXSS flaws in browsers are neither new nor uncommon[6]. We appreciate Mozilla’s and Brave’s efforts in enabling security researchers to not only report such issues, but also for fixing them with the highest priority to keep the users safe.
- 2019-10-15: Issue discovered and reported to Firefox.
- 2019-10-17: Firefox developers acknowledged and confirmed the bug as a security issue.
- 2019-10-17: Issue fixed on Github.
- 2019-10-22: Firefox for iOS v20.0 released with the security issue fixed.
- 2020-01-31: Same issue discovered in Brave for iOS[7] and reported to the Brave browser team via HackerOne.
- 2020-02-01: Issue was patched in Brave for iOS and a new version was released.
- 2020-02-04: Brave confirmed via HackerOne, that new version was published on the App Store.
Footnotes
https://developer.mozilla.org/en-US/docs/Web/Security/Same-origin_policy. ↩︎
Unlike the common XSS attacks, UXSS is a type of attack that exploits client-side vulnerabilities in the browser or browser extensions in order to generate an XSS condition, and execute malicious code. When such vulnerabilities are found and exploited, the behavior of the browser is affected and its security features may be bypassed or disabled. Source ↩︎
Critical vulnerabilities are urgent security issues that present an ongoing or immediate danger to Firefox users. There is no technical difference between sec-critical and sec-high vulnerabilities, they only differ based on the risk users are exposed to. Certain sec-critical vulnerabilities will cause an immediate dot-release to be issued—Source. ↩︎
https://en.wikipedia.org/wiki/Bookmarklet ↩︎
Some examples of UXSS bugs in Browsers: UXSS in Safari WebKit, Browser logic vulnerabiliteis, UXSS: Origin confusion when reloading isolated data:text/html URL, Firefox uXSS and CSS XSS, and UXSS in Chrome Android. ↩︎
We did not find the vulnerability in Brave in October, as the version of Firefox they were using was an old one. Brave did a release in November’19, which was based on the version of Firefox that had the security issue. Therefore, in our sanity check before publishing the blog post in Febuary we found Brave for iOS to have the same security issue. ↩︎